Outsourcing plays a vital role in all fields and Cybersecurity is no exception. This CSaaS guide explains what is cybersecurity as a service, its benefits & challenges along with some expert tips to leverage CSaaS:
Cybersecurity-as-a-service is a cybersecurity service offered by a third party to an organization or individual. This means an organization does not need to set up an in-house security and development team to build a robust cybersecurity management application or tool from scratch. Instead, it outsources its cybersecurity services or needs to a third party.
This cybersecurity vendor already has a developed cybersecurity platform or tools that an organization or individual can use via the cloud to protect their business from attacks. We have cybersecurity as a service company worldwide, always churning out different managed solutions to organizations to secure their infrastructures.
Table of Contents:
- Cybersecurity as a Service CSaaS Market: In-Depth Study
- Why is Cybersecurity as a Service Important?
- How Cyber Security as a Service Works
- Benefits of CSaaS for Businesses
- How to Implement CSaaS in Your Organization
- Types of Cybersecurity as a Service
- How Much Does Cybersecurity as a Service Cost
- CSaaS Vs Traditional In-house Cybersecurity
- Things to Look For in Cybersecurity as a Service Companies
- Challenges of Cybersecurity as a Service
- Expert Tips to Leverage Cybersecurity as a Service
- FAQ’s on CSaaS
- Conclusion
Cybersecurity as a Service CSaaS Market: In-Depth Study

Many cybersecurity-as-a-service solutions undergo rigorous testing before being released for public consumption. The cybersecurity as a service CSAAS market is a very huge and profitable one as it covers threat intelligence, auditing, monitoring, enterprise domain security, endpoint, cloud, network, and application security. According to statistics conducted, the cybersecurity market is expected to reach USD 56.6 billion by 2033.
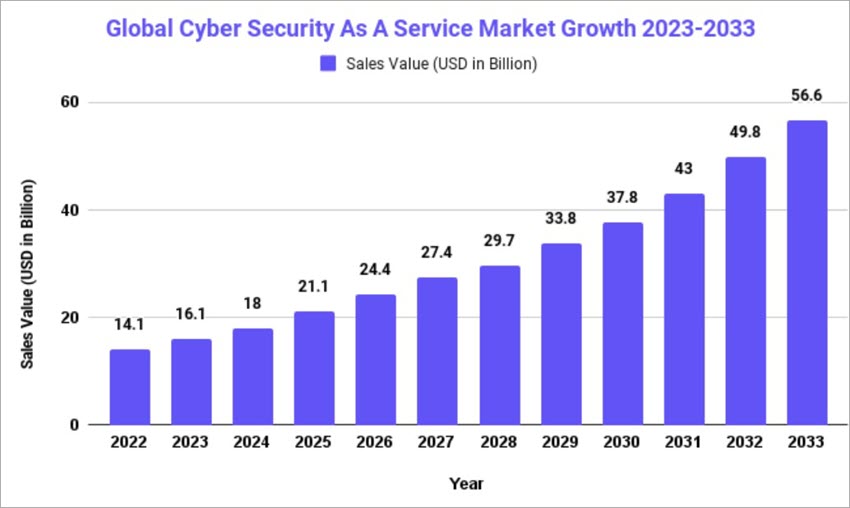
[image source]
Here is a video for your reference:
Why is Cybersecurity as a Service Important?
Data shows that cyber-attacks are on the rise with some even more sophisticated and putting a lot of pressure on companies to enhance their security posture and thereby spend more. As organizations are trying to defend their network using available technology, malicious actors are always moving a step higher in trying to find a backdoor they can use to attack a network.
It’s possible the in-house security team setup does not have adequate resources or the competence to defend an enterprise network, but a fully managed cybersecurity as a service can offer every organization a more cost-effective solution that can help address every possible cyber threat on an organization.
Also Read => A Complete Guide On Cybersecurity Analytics

[image source]
How Cyber Security as a Service Works
We need to understand how Cybersecurity as a Service works if we want to reap its full benefits. Cybersecurity-as-a-service combines the best security services, using the best security experts to design and develop a complete security solution.
In a traditional Security Operations Center (SOC) model, security experts will monitor, detect, identify, prevent, and resolve security issues. A SOC facility is not cost-effective. It contains sophisticated security software and tools that can help monitor and respond to your organization’s security threats. All these do not come cheap but at a high cost.
In a Cybersecurity as a service model, the technology that is used combines technology and human expertise to defend a network. It uses Artificial Intelligence (AI) and other sophisticated technology to manage incident response, endpoint security, application security, data security, and cloud security.
Benefits of CSaaS for Businesses
Many organizations are already using Cyber Security as a Service and deriving many benefits from it:
#1) Cost-Effective
Setting up a traditional security operation center can be capital-intensive and not cost-effective. With CSaaS your initial investments are less because you will not need to start hiring and training in-house security professionals to develop and manage security tools.
It is a cost-effective way of reducing both direct and indirect costs of maintaining an in-house team. It reduces direct costs for experts’ salaries, continuous training programs, and the setting up of advanced security tools. It reduces indirect costs for continuous maintenance and upgrades.
#2) Availability
Companies that provide cybersecurity as a service are now readily available online and it’s very easy to request a cyber security service or solution from anyone we think can offer us the best service.
#3) Post-Incident Analysis and Reporting
It has an advanced and enhanced reporting system that can provide real-time security status. It has a feature that helps to conduct and analyze every security incident to understand the root cause and impact. When you analyze these incidents report will help you know how to improve your security posture. These detailed reports help defend and protect your organization against cyber threats.
#4) Highly Scalable
Cybersecurity as a Service vendors develop solutions that are highly scalable In terms of urgent feature needs, it can be scaled up and down based on business needs, they offer a solution that is flexible and adaptable without causing business disruption and can easily be customizable, this solution can easily be tweaked using some Ad-ons that the solution can allow.
#5) Experts Availability
We have a group of cybersecurity experts who have deep knowledge and expertise in cybersecurity operations. Vendors know the importance of hiring and using highly skilled professionals who have in-depth knowledge of current threats, technologies, and best security practices to defend and protect customers’ businesses.
#6) Continuous Improvements and Updates
Cybersecurity as a service vendor always ensures that their tools and methodologies are updated with current trends in cybersecurity so they can be able to meet new challenges that the market may bring. These continuous updates help protect businesses against emerging cyber threats.
#7) Continuous Support
Vendors that provide cybersecurity as a service will always protect against cyber threats in a continuous loop. They try to minimize downtime as much as possible and give their customers a service level agreement (SLA) that states technical support response time.
The Vendor will always provide round-the-clock monitoring and support, which will allow for early detection of cyber threats and can immediately take remedial actions to reduce successful attacks.
#8) Regulatory Standards & Compliance
A Cybersecurity as a Service provider ensures that their solution meets regulatory standards and helps every organization operate their business on the best practices set by industries which minimizes the risk of penalties and legal matters. A vendor always ensures that their customers always meet regulatory standards and compliance requirements.
#9) Seamless Integration & Deployment
it is very easy to deploy and integrate with other cloud services, it is a plug-and-play service that an organization can easily set up and guarantee their desired protection.
[image source]
How to Implement CSaaS in Your Organization
There is a need for a strategic approach when implementing Cybersecurity as a Service for your business or organization:
Before implementing a CaaS there is a need to do a comprehensive analysis of the current cyber security posture of the organization to discover areas that need improvement. This analysis includes an evaluation of the security measures available, cyber threats, and cyber risks a business or organization may be exposed to.
#2) Choose your Service Provider
Research different CaaS available globally and perform due diligence on them to select a recognized cybersecurity service provider who can offer the specific services that meet security needs. Ensure adequate research is conducted to confirm the vendor’s track record, such as the customer reviews and industry certifications acquired, which will help in determining the best option.
#3) Develop the Plan
The type of cybersecurity service needed must be clear to the service provider, it must be a plan that aligns well with your business objectives. The plan must be detailed enough to include how the project will be executed, the project timelines, and different service agreements like the service level agreement.
#4) Initial Setup and Implementation
This is also part of what must be stated in the plan, the implementation must be done in such a way that it will not disrupt business operations. The cut-off process must be seamless and during this period all services must be up. There is a need to train people who will be managing the solution, but this does not stop the service provider’s availability to provide support as stated in the service level agreement.
#5) Continuous Monitoring
- Threat Detection: There is always an immediate response to security incidents through adequate incident management processes that include investigating, resolving the issue, and documenting the whole process as a pointer to a solution if such security incidents occur again. Advanced security tools like intrusion detection systems (IDS) can be used to carry out this task successfully. There must be due care that needs to be carried out to ensure regular assessments of the implemented security measures are effective, and working and captures emerging security threats. This means routine security audits, vulnerability checks, and penetration tests must be conducted to identify and remove any threats or vulnerabilities.
- Threat Prevention: The monitoring also includes the preventive part that involves measures such as software updates, patch management, and creating security awareness for employees. CSaaS providers ensure instant response to contain and mitigate any cyber threats. It uses advanced security tools like intrusion prevention systems (IPS), firewalls, and encryption to secure data by proactively blocking potential threats before they cause harm to your enterprise network as a whole.
- Post-Incident Analysis and Reporting: After any security incident, there must be a thorough analysis that is conducted to reveal the root cause and impact of the attack. This is done because of what can be learned from the incident and how that will help in improving security measures that can be used for any future security incident.
- Improvement and Updating: Regular security updates and security patches are very necessary to prevent and remove any vulnerabilities in the system. Malicious elements are regularly improving on their malicious attacks and there is a need to stay current with the latest security developments in other to have the capacity to handle new and emerging threats.
Types of Cybersecurity as a Service
When you deploy cybersecurity as a service to your business means you have now shifted the security watch of your business to a security vendor’s dedicated Security Operations Center (SOC).
#1) Network Security
Cyber security vendors can provide network security services to businesses by using sophisticated tools like advanced firewalls and intrusion prevention systems to block harmful traffic. There is real-time monitoring and threat intelligence that helps in identifying and removing threats.
Network security uses access control, encryption, and network segmentation to prevent your network from unauthorized access and ensures constant network monitoring to discover any real-time threat.
Endpoint security services are used to protect your network when you have devices that are connected remotely, this ensures that your connections are secure and your sensitive data are protected. It uses endpoint detection and response (EDR) tools and secure VPNs to provide and maintain security on devices outside the organization’s firewall. This Endpoint security can be maintained through regular updates and patch management.
#3) Cloud Security
This protects all cloud resources like data and applications deployed across multiple cloud platforms. The cloud environment can be secured using data encryption, Identity and access management (IAM), and backup features. It’s very important to conduct regular security audits and comply with regulatory standards, this cybersecurity cloud service also implements multi-factor authentication (MFA) to improve its cloud security.
#4) Data Security
This solution provides security to your enterprise-sensitive data using encryption, access controls, and data loss prevention (DLP) mechanisms. Data security services ensure that security policies about data security are implemented with adequate and constant monitoring.
Data security service ensures that an unauthorized individual does not have access to restricted or sensitive data. This solution ensures that data integrity is continuously maintained.
#5) Application Security
This helps conduct code review, vulnerability scanning, and configuration of web application firewalls (WAF) to secure deployed applications. It also involves following the best and most secure development practices through coding rules and development guidelines.
Some of these solutions help with scanning the source code in other to find code bugs and vulnerabilities and guide on how developers can fix the issue. Some solutions can be used to protect email and users from phishing attacks. Secure mechanisms such as multi-factor authentication (MFA) and threat intelligence are implemented.
How Much Does Cybersecurity as a Service Cost
Well, the pricing depends on several factors like the type of services needed and what models of the service you are subscribing to.
Depending on the scope or level of the security service needed, size, requirements, and complexity, we can get a Cybersecurity as a Service (CSaaS) between $50 – 500 monthly and $1000 – $5000 yearly. Though this pricing varies by geographical location, what is obtainable in the US may be different from what you get in Europe.
The service provider offers the security service in four different models:
- Monthly subscription
- Quarterly subscription
- Annually subscription
The client has the final say on the type of models they want even though the vendor can advise on the type of service that will favor their business. There are ready-to-use models and we also have those that can be customized per the client’s request and requirements. This subscription model is cost-effective and very scalable and can save an organization’s money and resources on setting up their in-house security team.
CSaaS Vs Traditional In-house Cybersecurity
CSaaS is different from traditional in-house cybersecurity because of its proactive nature, its monitoring and mitigation against threat is continuous. The traditional in-house is usually reactive, it deals with security incidents only after they occur.
CSaaS will ensure real-time threat detection and prevention which is different from traditional in-house cybersecurity that is post-incident. This real-time threat detection and prevention mechanism of CSaaS reduces the risk of cyber-attacks and data breaches and minimizes potential damage that could result from the attack.
CSaaS is very cost-effective and highly scalable, which helps alleviate the higher cost and limited scalability that is linked to traditional in-house cybersecurity. These services are offered by highly skilled experts in the industry which makes it a comprehensive and robust solution compared to in-house teams.
Organizations benefit from the latest security technologies and practices offered by CSaaS providers, you do not need to spend a fortune on infrastructure and training that is associated with traditional in-house cybersecurity.
Things to Look For in Cybersecurity as a Service Companies
#1) Continuous Support
Look for a provider that will offer you constant support in terms of security and monitoring capabilities, real-time threat detection, and response. A provider must have technical support online 24/7 to respond to any request and ensure effective incident management and minimized downtime which is crucial to business continuity. The provider must have an SLA in place that will highlight the importance of fast response times.
#2) Advanced Security Technologies
Another thing you need to look for when choosing a CSaaS provider is the level at which they utilize advanced security technologies in their solution. These solutions should have some of their features built with machine learning, artificial intelligence, and an automated threat detection mechanism which increases the ability and chance of identifying and responding to advanced and sophisticated threats faster.
#3) Industry Certification
The provider or vendor you want to deal with must have industry certifications like ISO/IEC 27001, SOC 2, and PCI DSS, Industry-specific certifications like HIPAA and GDPR are also critical when choosing a provider. Their in-house experts must have certifications like CEH, CISSP, CISM, CISA, and many more.
These certifications are critical when choosing a CSaaS provider as they indicate a high level of professional competency and adherence to industry standards. It validates the provider’s commitment to continuously update their knowledge on the rapidly evolving field of cybersecurity.
Challenges of Cybersecurity as a Service
All security solutions have pros and cons and the following are challenges to consider with an outsourced security solution:
- You don’t have full control over CSaaS security operations.
- Complex IT environments like having a legacy system both on-premise and in the cloud could pose a serious challenge to integration to a CSaaS solution.
- When you use a solution that has a negative review rating online may cause damage to your business.
- If a specific cybersecurity service provider is targeted, your resources or data may be at risk of getting leaked.
- If the solution is already vulnerable can put your business or organization at risk of vulnerabilities.
- Failing to implement and enforce policies that address risks to cloud security as stated by the service provider.
- When there is poor security architecture and failing to adopt an effective security framework may lead to malicious attacks.
- When there is poor integration planning, like underestimating the time, effort, and cost of cloud migration can fail.
- There could be cost challenges even when CSaaS solutions are generally cost-effective, it could still pose a serious challenge for small and mid-size businesses that may find it hard to kick-start with the service unless the provider offers flexible pricing models with reasonable monthly subscriptions.
Expert Tips to Leverage Cybersecurity as a Service
#1) Incident Responsiveness
You must carry out an evaluation of the CSaaS provider on their responsiveness to any security incident. There is a need to evaluate the provider’s ability to handle large-scale incidents when they occur. What was their experience when there was a major attack in the past and how they can quickly deploy their team during a breach?
#2) Seamless Integration with existing SIEM tools
When deploying a CSaaS to your enterprise network confirm it can seamlessly integrate with your current SIEM system without causing an obstruction or a gap in the monitoring operation. When this is done you will be able to accurately monitor and conduct threat correlation.
#3) Conduct regular reviews of threat intelligence feeds
There are currently multiple threat intelligence feeds for cybersecurity data. The reason why conducting a regular review of the threat intelligence feeds is very important is so that you will be able to cover the latest global threats that are relevant to your industry.
#4) Regularly review the Service Level Agreement (SLA)
Always review your SLA because business operations and the threat landscape always change. Ensure you adjust the SLA to include important details like the timelines, response, and remediation of security issues.
#5) Collaborate with CSaaS Security Team
You can set up a security model where your internal security team will collaborate with your CSaaS security team. This type of model helps you to have deep insight, control power, and advanced capabilities into the type of service the provider is offering you and how your internal security team can quickly respond to incidents without the provider’s interference.
FAQ’s on CSaaS
1. What is the meaning of Security as a Service?
When you outsource your cybersecurity requirements or needs to a third-party agent. This vendor manages and has complete insight into what an organization needs to protect its network infrastructure against intruder attacks.
2. What value does cybersecurity as a service provide organizations?
They provide an organization with the confidence that they can rely on their managed cybersecurity as a service to provide them with access to advanced security services without necessarily developing in-house security expertise.
3. What is SaaS in cyber security?
SaaS security is the practice of protecting software as a service (SaaS) applications against cyber-attacks. While the SaaS provider provides the platform for this service they also take care of the platform infrastructure security so that it’s not prone to cyber-attacks.
4. What does service mean in cyber security?
These are professional services offered to assist organizations in protecting their networks and data from intruder attacks, these services are usually part of the risk management plan drafted for an organization, they assess an organization’s security needs and recommend solutions to mitigate risks.
5. What is the best cybersecurity SaaS product?
We have many cybersecurity as a service products online, you will need to know what you want to secure on your network and the security features you require, this will assist you to know the type of security vendor to engage.
6. What is PaaS in cybersecurity?
Platform as a Service (PaaS) is a cloud computing model where a platform is provided for an organization to build, develop, run, and manage cybersecurity software..
7. Which software is used for cyber security?
There are so many free cybersecurity tools online. One of the most popular is Kali, which is open-source. This tool is very popular because it can be modified for different people with different levels of understanding.
Conclusion
The world is evolving so are the cyber threats. We have more sophisticated tools than before that can be used for unethical purposes today, and this lies the need for organizations to protect themselves against malicious attacks on their data and infrastructure.
It is usually good for an organization to adopt cybersecurity-as-a-service so they can stay focused on their core operations instead of getting overwhelmed with the burden of setting up a security operation center with adequate cybersecurity professionals running the day-to-day activities which is expensive.
Most of these cybersecurity as a service are plug-and-play with little or no stress in the configuration, what is required by the users is the management of these tools to achieve the main purpose of serving as the protective layer for any organization. I will advise you make research online for managed cybersecurity as a service that will best serve your organization or business purpose.








![How to Get Entry-Level Cyber Security Jobs [2023 GUIDE]](https://www.softwaretestinghelp.com/wp-content/qa/uploads/2023/10/How-to-Get-Entry-Level-Cyber-Security-Jobs.png)


