Learn how to integrate Amazon ECR with GitHub to automate the workflow of Docker images. This step-by-step tutorial will cover Docker image security and GitHub Actions integration for efficient container management:
Amazon Elastic Container Registry (ECR) is an Amazon Web Services (AWS) managed container image registry service that stores, shares, and deploys container images.
In the final part of this series, we will examine the Amazon ECR feature. This feature offers an image scanning capability that utilizes the Common Vulnerabilities and Exposures (CVEs) database from the open-source Clair project to identify vulnerabilities in Docker container images.
=> Check ALL Tutorials in Amazon ECR Series Here
Table of Contents:
Amazon ECR and GitHub Integration: Detailed Guide

In this part of the series, we will also explore integration with GitHub Actions to automate image build/pull/push operations using the workflow generated from Amazon Q. This GenAI-powered assistant provides fast responses to users’ queries.
Scan Docker Container Images for Vulnerabilities
Typically, we focus on the functionality, ignoring security, which is a major concern these days. To resolve this aspect, Amazon ECR can be set up to automatically scan on push and view the vulnerabilities that need to be addressed.
Amazon ECR uses the Common Vulnerabilities and Exposures (CVEs) database from the open-source Clair project. Static scanning of Docker container images happens before deployment, as opposed to dynamic scanning, which normally happens at runtime.
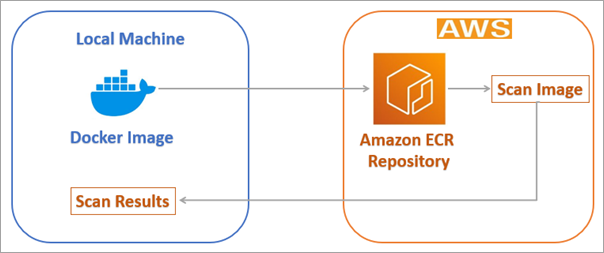
The vulnerabilities are shown in the console, or they can also be fetched from the AWS CLI. To enable Scan on push for the Amazon ECR private repository, select the repository and select Actions -> Edit -> Repository
Scroll to the bottom and toggle the Scan on push option.
Run the above Jenkins pipeline configured in the previous section. As the Docker image is pushed to the private repository, click on the version in the private repository in the Amazon ECR console.
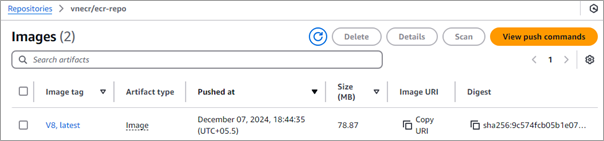
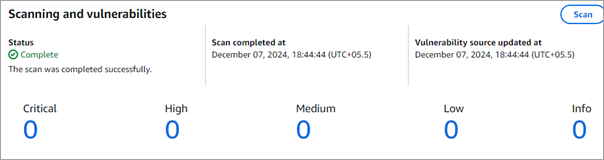
Click on V8, the latest image tag. Any vulnerabilities found will be shown. In this case, there are no vulnerabilities.
Push Docker Image to Amazon ECR Private Repository Using GitHub Actions
GitHub Actions is a built-in CI/CD platform in GitHub, with the help of which you can automate building, testing, and deploying applications.
GitHub Actions are typically event-driven, which means you can run a series of commands after an event has occurred. For example, when a pull request or a GitHub issue is created.
With GitHub Actions, you can create workflows that will build and test every pull request to your repository, which are triggered automatically when an event occurs. A workflow contains a job.
The job then includes and uses steps to control the order in which actions are run. Each job will run on a runner, which is a virtual machine or even inside a container.
GitHub Actions provides support for Linux, Windows, and macOS virtual machines. These runners can be self-hosted in your data centers or on the cloud.
A prerequisite to push Docker images to an Amazon ECR private repository is to have at least basic knowledge of GitHub Actions syntax and access to the Amazon ECR private repository.
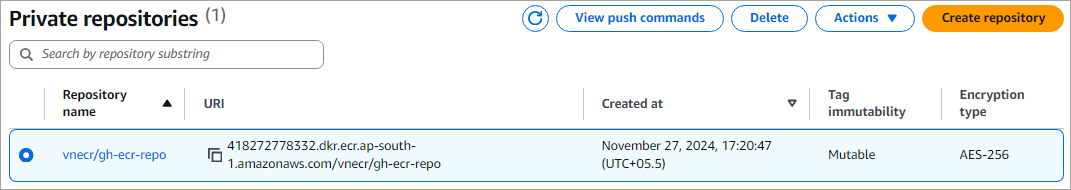
I have the following Amazon ECR private repository, which I will use through GitHub Actions.
Setup Amazon Access Keys Secretly in GitHub Repository
In our GitHub Actions workflow, I will need to reference the below Amazon Access Keys as secrets in our GitHub repository.
- AWS_ACCESS_KEY_ID -> The AWS Access Key ID
- AWS_SECRET_ACCESS_KEY -> The AWS Secret Access Key
- ECR_REPOSITORY -> The name of the private Amazon ECR repository created as shown above. Here, the value would be vnecr/gh-ecr-repo as shown in the above screenshot
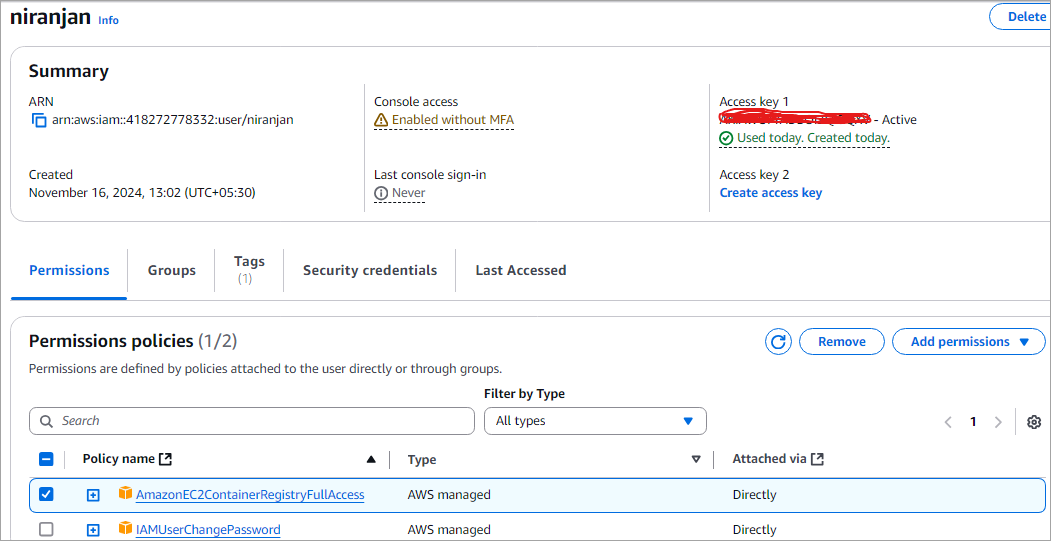
To get the AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY, go to the IAM service and CREATE a user, or for any existing user, modify the same and click on Create access key. Remember to save the values for the same.
For the user, edit the properties and ensure to attach the following policy AmazonEC2ContainerRegistryFullAccess by selecting Add permissions -> Attach policies directly.
Next, add the above secrets to your GitHub repository. Go to the repository Settings tab -> Security -> Secrets and variables -> Actions. Click on New Repository secret.
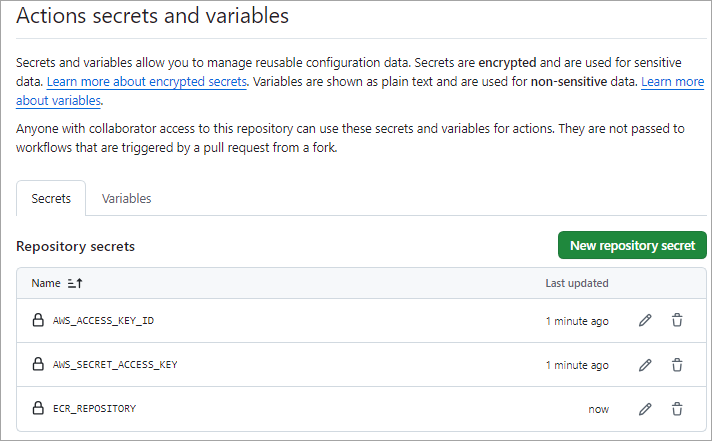
Create the GitHub Actions Workflow
Let’s create a custom workflow for the repository inside the “.github/workflows” directory to build and push the Docker image to the Amazon ECR private repository.
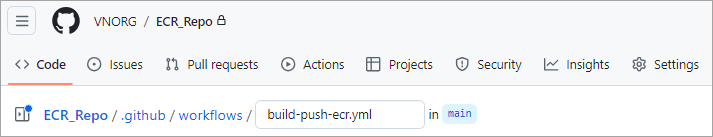
Now, to get the complete workflow, I asked Amazon Q, which is a GenAI assistant that helps to generate the code content for my needs and also accelerates software development. It is available as part of the AWS cloud platform.
I launched Amazon Q from my AWS account by clicking on the right-hand corner icon.
I entered the following prompt.
Create a GitHub Actions workflow to build and push a Docker image to an Amazon ECR private repository:
I got the following response with the code.
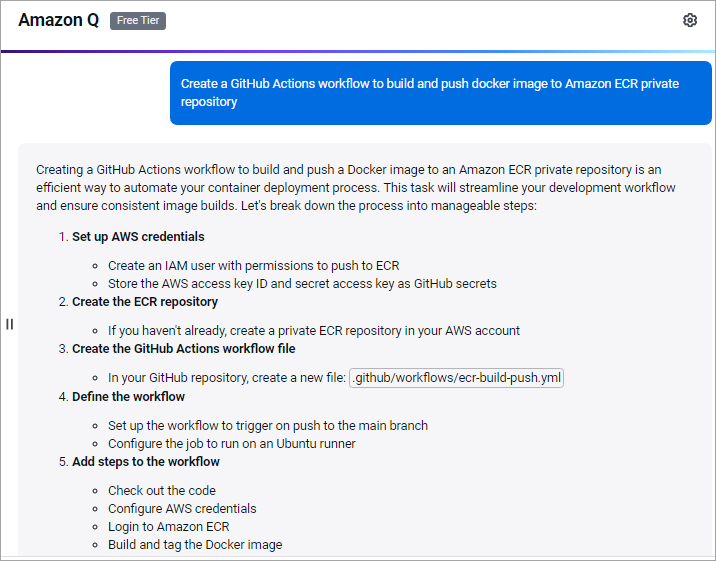
Here is the complete code added to the .github/workflows/build-push-ecr.yml file, which helped me deploy quickly with only making a small change in GREEN. The workflow will start the run once the code is committed to the main branch and will build, tag, and push the Docker image to the Amazon ECR private repository.
name: Build and Push to ECR
on:
push:
branches: [ main ]
jobs:
build-and-push:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v2
- name: Configure AWS credentials
uses: aws-actions/configure-aws-credentials@v1
with:
aws-access-key-id: ${{ secrets.AWS_ACCESS_KEY_ID }}
aws-secret-access-key: ${{ secrets.AWS_SECRET_ACCESS_KEY }}
aws-region: ap-south-1
- name: Login to Amazon ECR
id: login-ecr
uses: aws-actions/amazon-ecr-login@v1
- name: Build, tag, and push image to Amazon ECR
env:
ECR_REGISTRY: ${{ steps.login-ecr.outputs.registry }}
ECR_REPOSITORY: ${{ secrets.ECR_REPOSITORY }}
IMAGE_TAG: ${{ github.sha }}
run: |
docker build -t $ECR_REGISTRY/$ECR_REPOSITORY:$IMAGE_TAG .
docker push $ECR_REGISTRY/$ECR_REPOSITORY:$IMAGE_TAG
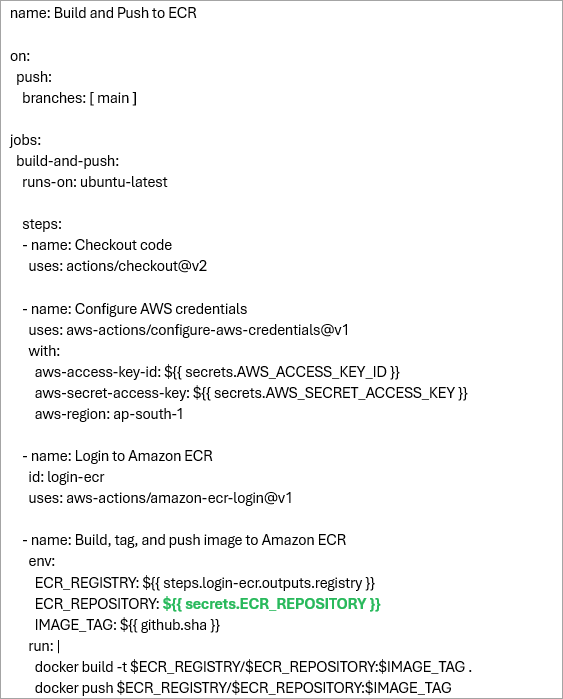
Copy the code to the YAML file and commit the code to the GitHub repository.
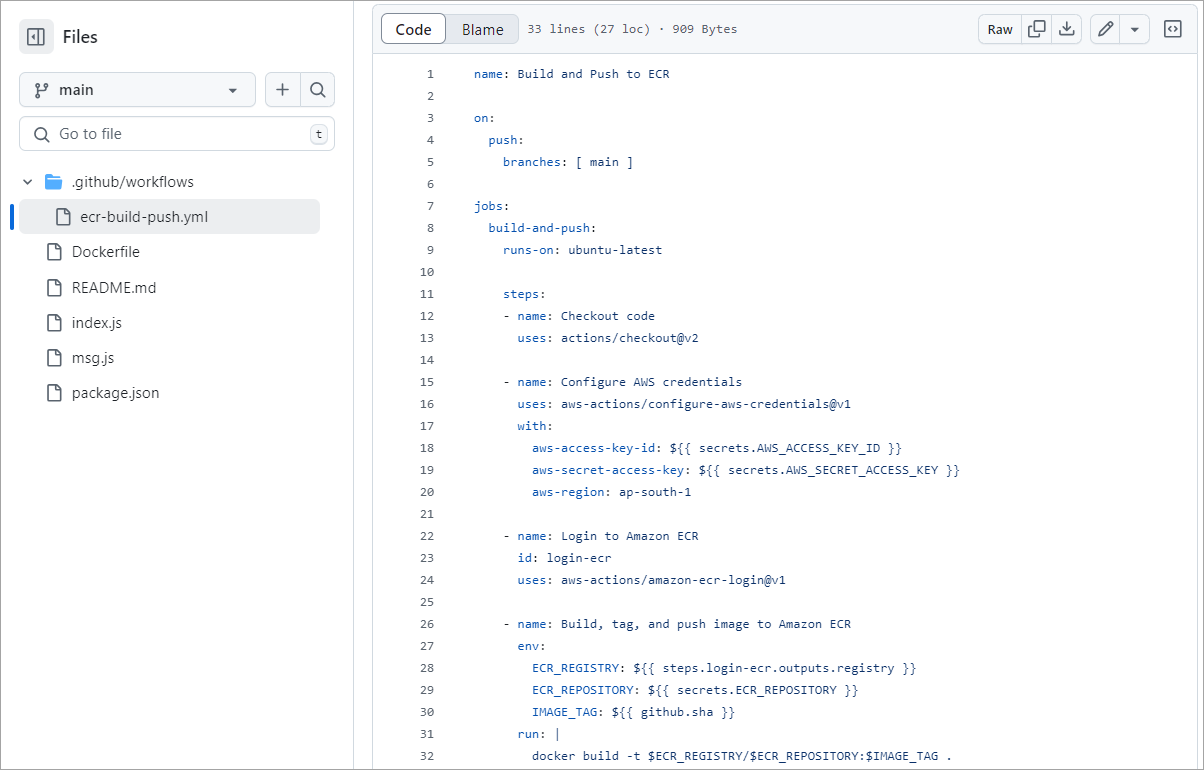
The workflow is run successfully and can be seen from the Actions TAB.
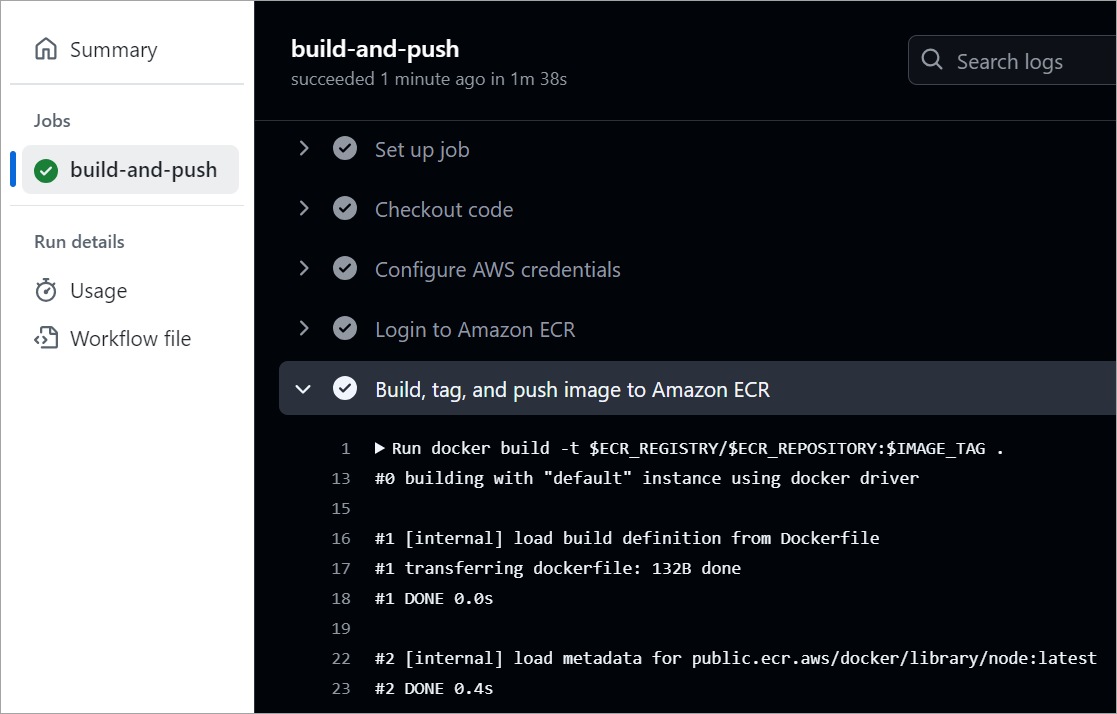
View the image pushed to the Amazon ECR private repository.
Key Use Cases of Amazon ECR
As we have seen, Amazon ECR is a fully managed Docker Container Registry as a service offered by AWS. It is a very essential component of container-based application deployment by providing a secure, reliable, and scalable repository for storing and, of course, distributing container images.
Some of the key use cases of Amazon ECR are:
- Provide a central repository for storing and distributing container images.
- Seamless integration with popular CI/CD tools like Jenkins, GitHub Actions, and AWS CodePipeline.
- Support for Docker Hub and other third-party registries to pull container images.
- Access control for container images controls who can push or pull images from the registry.
- Private repository support to ensure that critical and sensitive images are not exposed and are securely stored.
- Automatic image scanning helps find vulnerabilities, maintain, and deploy clean image versions.
Pricing for ECR
For AWS free tier accounts, you would normally get 500 MB of storage for private repositories and 50 GB per month for public repositories. You can also transfer 500 GB of data to the internet from public repositories anonymously without an AWS account.
If you have an AWS account as part of the free tier, you can transfer 5 TB of data to the internet from a public repository per month.
For pricing beyond the free tier, please visit https://aws.amazon.com/ecr/pricing/
Summary and Benefits of Amazon ECR
In this 3-part series, we have seen how Amazon ECR is easy to implement to push container images and pull images without using any tools or utilities. It shares and downloads images securely using the HTTPS protocol with encryption, and is fast and reliable for accessing/distributing your images.
Amazon ECR is also integrated with Amazon Inspector for image scanning of known software vulnerabilities, so the images are secure before you deploy them.
We also look at how to automate the Docker Build and Publish of the images to Amazon ECR public and private repositories using Jenkins and GitHub Actions, which is probably the way developers should work with, or for that matter, use any other CI/CD tool to automate manual steps, which is very much essential for modern-day development and deployment.
So, with Amazon ECR, developers can host their Docker container images in a highly available and scalable architecture without really worrying about the underlying infrastructure. Developers can then use the Amazon ECR Docker container images and seamlessly deploy to an Amazon Elastic Kubernetes Service (EKS) cluster.
For more quick GitHub & Docker-related guides, you can explore our range of tutorials below:
- GitHub REST API Tutorial – REST API Support In GitHub
- Docker Tutorial: Installation And Introduction To Docker
- Comparison Between Kubernetes Vs Docker
- Project Planning with GitHub Projects
- What is Docker Compose? Installation and Volumes with Examples
PREV Tutorial | FIRST Tutorial







